
Click on the following hyperlinks for more information regarding various types of security devices:
Security Equipment Display RoomSecurity Products
Access Control Systems are designed to ensure that only the people that should enter premises or areas are allowed to do so. Access control systems may use very sophisticated technology or they may be very simple and merely rely on a security guard or other person simply checking identification documents. But whatever type of business you operate, you need to control the people who enter your premises every day. Failure to do so will permit an unauthorised intruder free access, and the opportunity to commit a crime. However, Access Control Systems should not obstruct the easy entry of authorised persons and and should be chosen carefully to meet the needs of the situation.
What is an access control system?
Any system that limits entrance and exit to those who have been authorised may be called an access control system. Controlling the access of a person is a three-stage process:
- authentication of the person's identity;
- granting of entry to an authorised area at an authorised time; and
- control of movement within, and exit from, the authorised area.
Why you need an access control system?
Reliable access control is a critical element in any area protection plan. Security features designed to keep criminals out such as alarm systems and so on, are useless if there is no control on persons who are allowed to enter a given area.
Common types of access control systems
Access control systems use different technologies, or a combination of technologies, to recognise an authorised user. Identification of the person seeking entry can be achieved by:
- a human system, for example a security guard checking who enters an area;
- the many different forms of card systems;
- what a person knows (the code or accompanying PIN number to be entered on a keypad);
- what a person is (biometrics systems using the different distinct features of the human body, i.e. a fingerprint, the iris etc.).
Enforcement of the rules
Once a system has been chosen and installed, the operation of the system must make up a component part of the overall security policy of the commercial enterprise. Such a policy must be enforced at all times at all access-controlled points and should be applicable to all staff members. The security policy should be clearly stated, and guidelines drawn up for staff to follow.
Biometrics





|
|
Cards      
|
|
Door Phones      
|
|
Hybrid     
|
|
Keypads    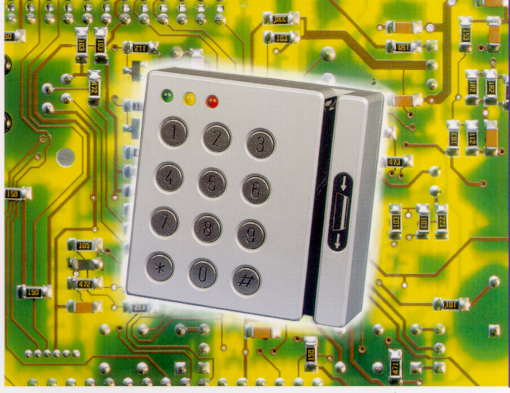
|
Why use an alarm system?
Alarm systems are designed mainly to warn of unauthorised access to
premises or attacks on persons, premises or installations such as safes.
Every year in Hong Kong millions of dollars are stolen from businesses
and private residences. Alarm systems can help prevent this by warning
the owner of the business or premises of unauthorised access and
allowing the owner to respond to that attack by, for example, informing
the police.
Types of alarm systems
There are different types of alarm systems available. There are two main
types; audible and silent.
An audible alarm is one where the activation by an intruder or other
person results in an audible sound such as a bell or siren.
A silent alarm, also known as remote or monitored alarm, is one where an
activation results in signal being transmitted to a monitoring station
where the person monitoring the signal informs the police or initiates
some other response to the alarm.
Alarms can also be a combination of both types; the idea is that the
audible alarm acts as a deterrent to intruders causing them to flee from
the scene whilst the remote monitoring of the system ensures that the
scene is attended by a police officer or other person.
The other choice in alarm systems concerns the type of sensor or sensors
used and this would depend on a number of factors such as the nature of
protection required, budget, etc.
Alarm systems can be used in a variety of situations; to detect
unauthorised entry into premises of any kind, to detect tampering with
safes or other devices/installations requiring protection, to detect
removal of items, for example paintings in a gallery or expensive items
in a shop, and so on.
Choosing your alarm system
There are many companies, which sell, install and provide maintenance
for alarm systems. Make sure you acquire your system from a reputable
company licensed by the Security and Guarding Services Industry
Authority.
Security alarm equipment requirement
All intruder alarm sensors, detectors, control panels and signalling
equipment should be designed to meet the American Underwriters
Laboratories (U.L.) Standard, British Standard 4737, or equivalent.
Check whether the system to be supplied to you meets the
requirement.
Security
Make sure that the authorized personnel who operate your alarm system
are familiar with how it works. This will help reduce false alarms.
Furthermore, ensure that details of the system and other security
aspects are not divulged to unauthorized persons.
Panic Alarm
A panic alarm normally consists of a either a “button” or other device
such as a “kick bar” which allows an employee to discreetly activate an
alarm when a threatening situation exists, for example, during a
robbery. Panic alarms are commonly used in financial institutions,
jewellery stores and establishments where goods of high value are kept
or stored. They may also be installed as part of a domestic alarm
system. Panic alarms can be connected to a monitoring centre or to an on
site control room or they may activate an audible bell/siren only. The
system can also be configured to activate CCTV recorder to record the
event. The alarm can be used to request emergency assistance from local
security, police or emergency services.
Activation    |
Alarm Transmission Line Monitoring     |
Detection     |
|
Electronic Article Surveillance    
|
CCTV is commonly used in commercial situations, for example in retail premises. Nowadays, CCTV cameras can be found in virtually every type of building with the exception of individual housing units. In Hong Kong, CCTV cameras are installed in the common areas of residential buildings as well as every type of office building or other commercial operation. In short, CCTV cameras can be found everywhere you look in Hong Kong.
The technology used in CCTV systems is constantly evolving and becoming more sophisticated. In recent years, advances in digital technology have resulted in the recording systems attached to CCTV cameras are now of unprecedented high quality with the result that images from CCTV systems are more useful when trying to identify suspects involved in a crime or other incident. CCTV systems cannot prevent crimes but they can assist in identifying culprits and as such can often deter crime. Even if systems are monitored by human operators, things are often missed as the operators’ attention begins to diminish after twenty minutes of watching a monitor. However, state of the art systems now incorporate various types of technology collectively known as “video analytics” which can identify various activities and activate an alarm and thus get around the problem of human operators.
If you or your business wish to install a CCTV system, there are hundreds, if not thousands of systems to choose from. Whichever system you choose though, should be installed in a way that will make it easy for the police to obtain copies of the images for evidential purposes in the event of a crime. The guidelines below will assist you in ensuring that your system helps the police to help you.
Cameras    
|
|
Control Systems     
|
|
Peripherals     
|
|
Remote Monitoring Systems     
|
How can you know that the security guards you employ are doing their job properly? The answer is to use a Guard Monitoring System (GMS).
These systems utilise technology to monitor the activities of security guards during their inspections and patrol tours, and normally work by the guard carrying a hand held electronic device – called a “Patrol Baton” – that is used to “make contact” with another device – called a “Reader” – installed at a fixed point where the guard is required to visit. When this is done, a signal is sent to a control room to confirm that the guard has visited the location (and keeping a record of it) or, more importantly, if the signal is not received within a certain time frame, that the location has not been visited and that there is a problem that needs to be investigated.
One of the most effective GMSs is the multi-point monitoring system. This consists of “readers” at various visiting points, strategically positioned throughout an installation where guards are deployed who are required to visit at pre-designated intervals. The Security Guard touches this reader with his patrol baton at each point to record the location, date and time of the patrol. These patrol batons are available in a variety of forms, including iButtons, Proximity Tags and Barcode. Each time the Security Guard touches the reader the information is sent to the Control Centre.
Another effective GMS is the Single Monitoring System; however, this is mainly used to monitor the performance of stationary guards at single points of entry, e.g. guardhouse or an entrance to a secure area in a building. The monitoring system, i.e. the reader, is activated when the guard touches it with his baton to acknowledge the fact he has arrived at this designated point. The signal is sent to the Control Centre where it informs the management that the guard has arrived.
There are many advantages to using GMSs. These include keeping track of employees (especially those working alone), maintenance workers, or for monitoring/tracking employees or contractors “on-site” and “off-site” times. However, most of all, GMSs allow businesses to observe or oversee the movement of security guards whilst they are on duty. It is a cost effective way of monitoring guards on site. The idea is to use technology to monitor the guard from a control room continuously to ensure that he/she is performing the duties assigned, and conducting tasks to the required standards. A GMS, can be ‘stand alone’ or can be integrated as required with other security systems, e.g. intruder alarm or access control. Just as important though, these systems alert Control Rooms when there is something wrong and allow a response to be initiated.
With the products now available it is possible for security managers and supervisors to monitor the movements and timings of their guarding personnel throughout the course of their tours of duty at pre-determined times; e.g. 15, 30 or 60-minute intervals. Such systems are invaluable management tools for record keeping, ensuring operational efficiency and confidence in your guards. Guards will perform their patrols as directed knowing they are being monitored throughout their tour of duty, thus avoiding the temptation to sleep, or walk off the premises during the periods when they should be performing their inspection patrols. This will result in a more secure and well-guarded site.
Guard Monitoring Systems       
|
Lighting is a very important component of any security plan. Adequate lighting of premises and surrounding areas can not only deter and detect unauthorised intrusion, but also make movement within the building visible from the outside – an important consideration when the premises are closed or unoccupied.
Good lighting facilitates surveillance and limits the opportunities for would be intruders or culprits to hide. Lighting should be used to complement physical and electronic security systems and help Security Officers to maintain visual contact during the hours of darkness, especially in sensitive areas or structures within a perimeter that is under observation. Therefore, lighting can help prevent crime in domestic as well as commercial situations and should always be considered.
Lighting is easy to install and quite cheap to maintain; however to get maximum performance from any lighting system requires a high level of technical knowledge. If used to optimum levels it could reduce the need for security personnel. It must also be borne in mind that lighting can also enhance personal protection by reducing the number of areas for a determined intruder to conceal himself/herself.
Consideration should be given to the type of lighting system that is required, which should be evaluated when determining a building/complex/area’s overall security requirements.
Security Lighting generally requires less intensity than normal working lights. Each location presents its own unique requirements, depending on physical layout, terrain, climate and security. Lighting manufacturers are the ones best placed to advise on these issues. When planning a security lighting system consideration must be given to local weather conditions, power source, back-up systems, lighting for CCTV systems, remoteness, lighting of adjoining buildings, environmental impact, recurring and maintenance costs and protection of equipment.
Lighting should be kept on at all times during the hours of darkness (i.e. half an hour after sunset and half an hour before sunrise). The use of energy is a major consideration when considering what type of lighting should be used. Some of the various types of lighting available are listed below:
Filament Lamps – These provide full light output immediately and are suitable for illuminating checkpoint areas.
Tubular Florescent Lamps – These come closest to the ideal lamp. They provide instant lighting and are very economical. However, they are not suitable to the outdoors.
Low Pressure Sodium Lamps – This type of lamp is extremely useful for high levels of illumination at short distances. They are very good for detecting intruders at long distances exceeding 50 metres.
High Pressure Sodium Lamps – These are currently the most favoured for security as they are highly efficient and have a long life.
Overall, lighting is one of the most effective and economical methods of reducing the threat of crime, and its value should not be underestimated when considering the installation of security systems. There is a tendency for security managers/consultants to concentrate on alternative and more expensive security solutions, with the inclination to ignore the importance of a good all-round lighting programme. It cannot be stressed enough that when installing a security system that lighting should be a part of that set-up.
General   
|
|
Passive Infra-red Activated   
|
Locks come in many shapes and sizes and offer different degrees of security. A lock may be no more than a token barrier that can be easily overcome or it can offer a high degree of security especially when used in conjunction a solid well-constructed door and other security devices such as alarm systems and CCTV.
What is a lock? A lock is a mechanical fastening device, which may be used on a door, vehicle, or container, restricting access to the area or enclosed property. Locks may be entirely mechanical, or electromechanical. They may be operated by turning some form of removable key, by keying or dialing in a combination which directly or via electromechanical means operates the lock, with some form of magnetic or other card reader, or by moving a part on a safety lock intended to prevent accidental operation rather than to prevent unauthorized access.
Door locks vary in types and sizes; the most commonly used are (i) ‘Rim Locks’ (which are fitted to the inside surface of the door), (ii) ‘Mortise locks’ (require a pocket—the mortise—to be cut into the door or piece of furniture into which the lock is to be fitted) and (iii) Cylindrical Locks (a cylinder that a locksmith can easily unscrew to facilitate rekeying. This lock may contain any of a variety of locking mechanisms, including the pin tumbler lock, the wafer tumbler lock and the disc tumbler lock).
Locks are categorized by the method in which they are operated.
- The Latch (This is a Spring Operated Bolt that operates automatically when the door is slammed)
- Deadlock (This mechanism can only be moved inwards or outwards by the key)
- Hook/Claw Bolt (This bolt is shaped in the form of a hook and specifically designed for use on sliding doors and metal gates, however this type of lock can also be used on any type of door).
- Two-Bolt Lock (This is a Latch and a Deadlock in the same fitting. It has a spring latch bolt that is operated by a handle on both sides of the door and a dead bolt operated by a key, again on both sides of the door)
- Nightlatch (This type if latch can only be operated on the inside by a knob and key on the inside).
If you expect a lock to provide a level of security, the lock should conform to a standard such as British Standard 3621. This standard (and other similar standards) specifies such things as how much pressure the lock can withstand, how many possible key combinations there are and so on. By using a lock that conforms to this standard you may be assured that you have a particular level of security. But remember that a lock is only as good as the door it is fitted to.
Padlocks
Padlocks, like other types of locks, come in a variety of shapes and
sizes and can offer a high degree of protection in certain
circumstances. Padlocks are normally used in temporary or outdoor
situations such as building sites or outside storage areas.
The distinguishing feature of a padlock is that it uses a shackle rather
than a bolt as the device to fasten two or more objects together. The
shackle is passed through the staple of a padlock bar.
Keys
With every lock comes a key. Without the key, locks cannot be used. Keys come in various forms and should only be issued to reliable and trustworthy staff. There are various types of keys you may wish to consider when formulating a security plan, ranging from the conventional metal key to high-end security locks, which cannot be replicated. Keys can be made up of words and phrases, electronic chips or magnetic strips, encryption devices or media applications for storing electronic data.
For the conventional metal key it is important that movement of keys be monitored preferably in a ‘Key Movement Register’. This way, the movement of keys can be checked or audited if lost or missing.
Duplicate keys should be made and kept separately in a secure place and should never leave the premises. They should only be used in emergency situations.
The importance of good locking mechanisms cannot be over-emphasized; and should form an important feature in any security plan. If used properly they will prove to be extremely effective.
Information on various locking mechanisms can be found below, however should further assistance or information be needed please contact the Crime Prevention Bureau, who will be happy to help with your enquiries
Combination Locks     
|
|
Electronic Locks     
|
|
Mortice Deadbolts     
|
|
Padlocks | Chains     
|
|
Rim Locks     
|
|
Hinge Bolts     
|
|
Window & Balcony Locks     
|
Perimeter protection refers to physically defining the limits of premises for access control purposes. It is an important facet, as it is accepted that trespassers can get through a perimeter in a time between 4 and 40 seconds. Perimeter protection or fencing is a great deterrent, and can be built as a strong decorative fence with heavy iron or a chain link fence with barbed wire offsets and coiled razor wire. Perimeter protection should also:
- Prevent and help to identify any attempt at trespassing.
- Delay intruders with a view to increasing the chance of making an arrest and prevent removal of stolen property.
- Guide and control pedestrian and vehicular traffic in the area of premises, and assist in identity verification.
In Hong Kong perimeter fencing can be grouped into the following categories:
- Industrial Chain-link Fencing;
- Expanded Metal Fencing;
- Masonry Walls;
- Palisade Fencing.
The most commonly used perimeter protection in Hong Kong is the Industrial Chain-link Fence, which can be found surrounding industrial sites/installations. It is not popular in residential areas or in service industries sectors due to aesthetic considerations. As a rule all fencing should reach a height of 2.5 metres, and supported by at least three strands of barbed wire or razor wire.
Perimeter fencing, although a deterrent, should be supported by an intrusion detection system. This could be in the form of Lighting or Motion Sensor Detectors or CCTV, or a combination of all of these. Lighting is particularly important as it provides a real and psychological deterrent to would be intruders, whilst at the same time allowing Security Staff to maintain visual presence during the hours of darkness. The installation of the other items mentioned would alert security staff to the immediate presence of intruders.
An important feature of the security fence is the point of access. This should be protected by a controlled point of access, ideally by a gate. The gate should be equal in height to the perimeter fence and extend to within two inches of the ground.
You must bear in mind that no two perimeters to any building or complex are the same, and each provides different challenges and solutions. The Officers of the Crime Prevention Bureau are available to provide advice to anyone seeking guidance in the installation of perimeter protection.
Fencing   
|
|
Gates & Barriers   
|
|
Perimeter Intruder Detection Systems 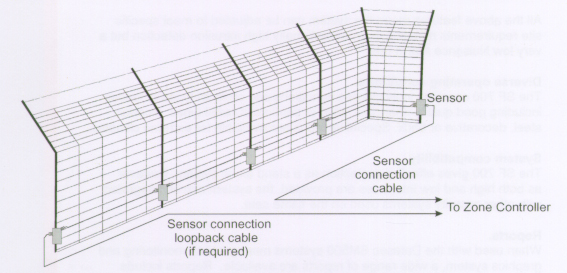
|
A personal panic alarm is an electronic device that consists of a switch and a small speaker that will sound an alarm when activated. There are several brands of panic alarms and while they may differ in features, they all have one purpose – to sound out a loud alarm when activated. This is to draw attention to the user, call for help in case no phone is available or if the user is incapacitated and, most importantly it can be used to scare away an intruder or an attacker.
There are several options to choose from when purchasing a personal panic alarm. Some are designed to be used in the home, where the elderly or physically incapacitated can make use of them, while others are designed to be carried around.
The handy personal panic alarm is a small handheld device, which comes with a switch button or pin. In case of an emergency, the user simply has to press on the button or pull the pin to activate the alarm.
Personal Panic Alarm   
|
Security Marking is a simple, low-cost and highly effective way to
safeguard many types of property. For maximum deterrent effect, the
marking must be readily visible and permanent, making the property
worthless to the would-be thief. In the event that marked equipment is
lost or stolen, it is easily identifiable as such, and so there is a
better chance of reuniting the property with its rightful owner.
Marking Property, or Security Marking is an extremely effective, simple,
low-cost and highly effective method of deterring thieves from stealing
property. Permanent marking either by engraving, scribing, ink systems –
or any method that enters the surface of the property has the following
benefits:
- Permanently and visibly marked property is obviously identifiable and deters thieves.
- Permanent and visibly marked property is good evidence as it is difficult to explain away and is easily traceable. Burglars and handlers of stolen property dislike well-marked property because anyone found in possession of it is likely to be convicted of an offence.
- The resale value of well-marked property is considerably less as few people want to own or possess it. How many people would buy equipment with someone else’s identity marked into the surface? Even if the marking is gouged out, the item is defaced, and its value is reduced even further. Thieves want to dispose of stolen property quickly, easily and profitably.
The best-known and most common form of marking is by Ultra Violet (UV) pens. This inexpensive method is a quick and simple to do and is not visible to the naked eye. Where UV is the sole method of marking used, it will only be useful if the property is recovered and checked with an UV lamp. One note of caution though, UV ink can fade over a period of 12 months if exposed to strong sunlight or heat; therefore marking should be reapplied on a regular basis.
Other available products include (a) Property Marking Solutions, both invisible and permanent. (These solutions contain unique elements of either DNA, UV or Micro dot), (b) Engraving (use scribing pens, ceramic marking pens or electric hand engravers), and (c) Etching (use a chemical solution and stencil)
Labelling is another effective form of marking property, as it can be applied as a visible deterrent to property. Labels can be tamper resistant or glued on with specialist adhesive that is difficult to remove. Some products leave a UV trace if removed. These will act as deterrent to thieves as well as making the property traceable and less sellable. These products, or, property marking kits can be bought locally, or through the Internet, where the choice and variety are much greater. Whichever method is used, the mark should be so secure that removing it would damage the property or affect how the item performs.
Property marking is particularly useful in a corporate or large institutional setting where there are large inventories of equipment that have to be kept track. Apart from the crime deterrent aspect of property marking, ensuring that all of a company’s or school’s office equipment is marked, makes better management of this inventory easier. Remember that employees are not always as honest as employers would like and conspicuously marked equipment is less likely to end up in employees’ homes!
Property Marking   
|
Suspect mail or parcels can be screened for different types of threat, using various types of screening equipment such as x-ray scanners and electronic sniffing devices. Mail screening is particularly important for organisations such as government offices, consulates, multinational companies, etc
Screening Equipment  
|
Cash, valuables and other important property should be stored in secure containers or facilities, e.g. safes or vaults, etc. Ideally such storage facilities should be immovable and protected in depth by other security devices.
Key Storage   
|
|
Safes   
|
|
Strong Rooms   
|
Theft of or from vehicles is a major concern in Hong Kong. In the past, vehicles have been stolen in Hong Kong and then loaded onto speed boats with China being the intended destination. However, in recent years criminals now disassemble the stolen vehicle before loading the parts into crates and shipping them to other South East Asian Countries. As a result the recovery of these vehicles is extremely difficult. With this in mind vehicle owners should consider investing in security measures for their vehicles.
Vehicle security systems can be divided into two main categories: mechanical or physical security and electronic security. Their main purpose is to protect the vehicle from being stolen or hijacked.
Mechanical/Physical Security
Physical security appliances involve the fitting of mechanical devices in order to prevent or delay the vehicle being removed. The vast majority are key operated locking mechanisms, which makes it important that the key to this device is not kept on the same key ring as the car keys. (A common oversight by the owner).
Some of the more popular security mechanisms are:
Immobilisation Device: This provides a locking system that cuts off fuel or electricity supply to the engine, thus making it impossible to ignite the engine. It’s common for this type of system to be in view as this would deter the criminal from breaking into the vehicle and causing damage.
Steering Wheel Lock: This is a strong metal bar, which is attached to the steering wheel of the car in such a way that it is impossible to move the wheel at all, or to restrict such movement, which would make it impossible for anyone to drive the vehicle.
Brake/Pedal Lock: This is a strong metal fitting that when locked to the brake or clutch the pedal allows little or no movement, again, making it impossible to drive the vehicle away.
Gear Stick Lock: This is available for both manual and automatic operating gear boxes. It’s a strong metal fitting, which is attached to the gear stick in such a way that makes it impossible for the criminal to choose a gear in order to drive away.
None of the above systems are guaranteed to stop your vehicle from being stolen but they will deter less determined thieves and even professional criminals will prefer to look for vehicles without security devices.
Electronic Security
These include (a) Alarm Systems, (b) Tracking Systems and (c) Number Plate Recognition Systems
(a) Alarm Systems:
The purpose of installing such a system is to give a warning signal that a criminal is trying to steal a vehicle. Today, there are a wide variety of alarm systems available on the market today. Generally, car alarms will sound an audible alarm such as a siren or something similar and when activated, will normally prevent the car from being started. More sophisticated systems include some kind of notification of the owner that his car is under attack. When considering car alarms the following features should be present:
- The system should automatically activate when the vehicle is parked, or when the driver activates the alarm after locking the vehicle;
- The alarm should be designed to sound an alarm when there is an attempt to break into the vehicle, which should cause the lights to flash;
- The alarm should be programmed to cut off the audible alarm after five minutes to comply with noise legislation in Hong Kong;
- There should be a standby electricity supply;
- The system should automatically cut off fuel or electricity supply to the engine when the alarm is activated;
- There should be a highly conspicuous warning to potential thieves to deter any attempt at theft in the first place.
(b) Tracking Systems:
The recent advancement in communications technology has made it possible for alarm systems to be linked to real time tracking of the vehicle after it has been stolen and the alarm triggered. In addition to this, these systems permit the tracking station to deactivate the engine by remotely cutting off the fuel or electricity supply. It is becoming more common for normal motorists to subscribe to these services. In fact, insurance premiums now reward the use of these services and individuals who subscribe to them find their premiums are reduced.
These systems also allow the installation of a panic alarm in the vehicle, which enables the tracking station to immediately locate the vehicle. Such a service is extremely useful in cases of vehicle hijacking but is probably more appropriate for cargo vehicles and other commercial types of transport.
(c) Number Plate Recognition:
Car park management companies typically use these systems, as they permit the vehicle registration number to be linked to a specific parking permit/ticket, thus preventing criminals from stealing vehicles.
Vehicle Protection Systems   
|